Collaborative Confidential Computing: Pioneering Data Privacy and Protection
Confidential computing is at the crux of today’s data-centric world. As data security concerns amplify, the spotlight is increasingly on collaborative confidential computing (CCC). This is an aspect of computing where multi-party collaborations are paramount.
At the recent Confidential Computing Summit held in San Francisco, Bruno Grieder elucidated on the nuances of Collaborative Confidential Computing, highlighting three pivotal technologies propelling it: Secure Multi-Party Computation (sMPC), Fully Homomorphic Encryption (FHE), and Secure Hardware Enclaves.
Collaborative Computing Deep Dive
As a bit of context on our work at Cosmian on Collaborative confidential computing, we are rooted in France and delve deep into the realms of cryptography. We craft encryption modules for a spectrum of clients ranging from large corporations, fintechs, to medtechs operating in the cloud environment. Through our consistent work with cryptographers and academic bodies, we ensure that we’re at the forefront of data protection and security, positioning us as the go-to solution for businesses desiring robust data protection, especially in the shadows of regulations like GDPR and Cloud Act.
The confidential computing model we champion involves a medley of players: data providers, code senders, result viewers, facilitators, and cloud hosts. The crux of the challenge in this secure environment is ensuring impeccable privacy and security. Every participant has an innate desire to protect their sensitive inputs from their peers.
In his presentation, Bruno Grider contrasted diverse methods via a blueprint that demands particular attributes, including encryption, multi-client inclusivity, validation, compatibility with advanced languages, operational efficiency, and streamlined deployment.
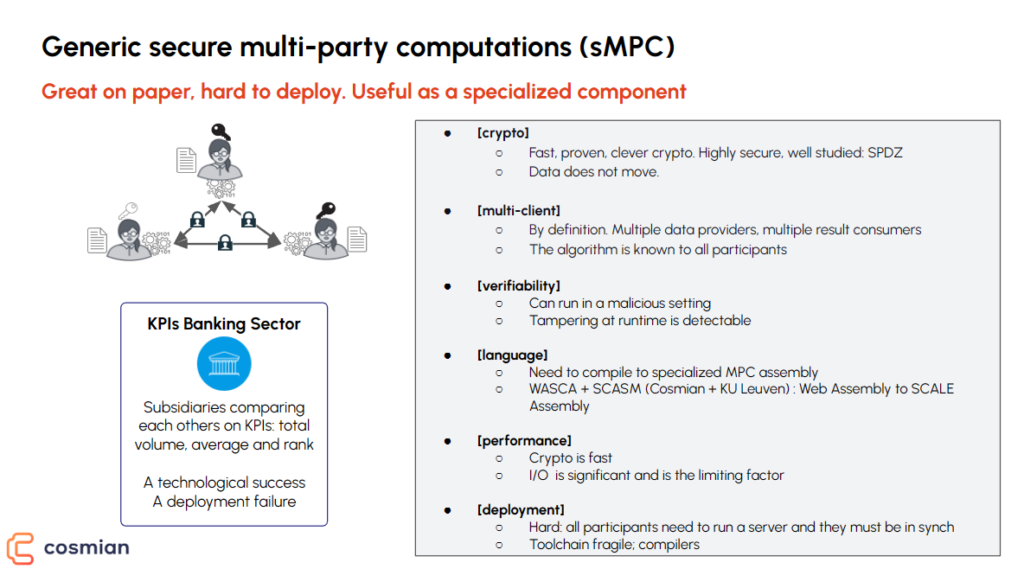
– Secure Multi-Party Computation (sMPC):
sMPC offers a paradigm where many can work collaboratively on encrypted data without ever unlocking it. It’s a bulwark of data privacy and security, facilitating operations like summing, multiplying, and discerning. Nonetheless, while sMPC is a stellar model of security, its broad-spectrum deployment faces hurdles. These are primarily because of intricate workloads and synchronizing challenges among the involved parties. Consequently, sMPC might not be the universal solution, especially for endeavors involving multiple stakeholders.
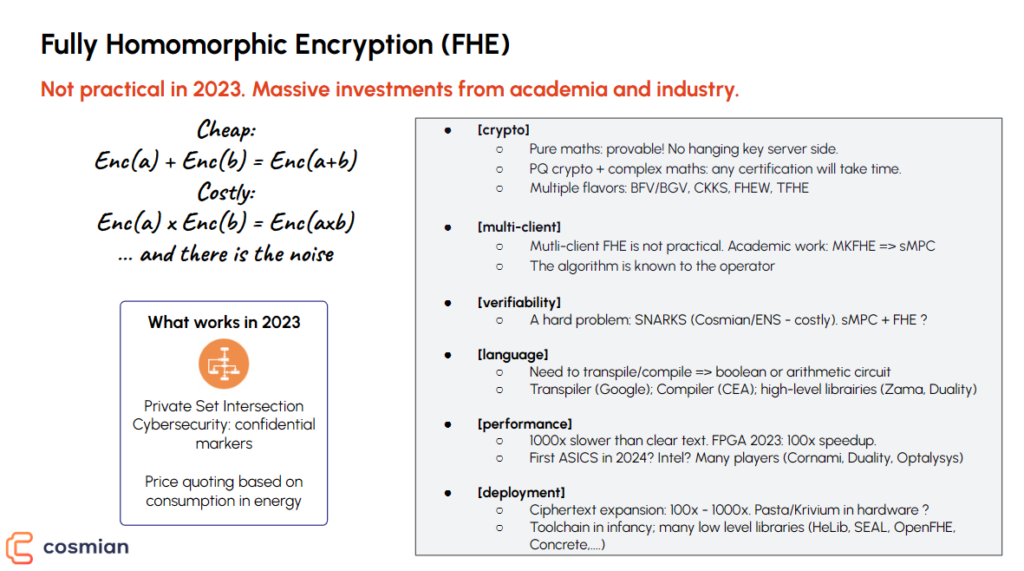
– Fully Homomorphic Encryption (FHE):
FHE is a state-of-the-art encryption method that allows for operations directly on encrypted data, ensuring data privacy throughout. Although it has the potential to reshape the data security landscape, current barriers, like immense computational demands and bloating of the encrypted code, render it less efficient than raw data computations. Ensuring trustworthiness and bridging different FHE implementations are still significant challenges.
– Secure Hardware Enclaves:
Often referred to as TEE (Trusted Execution Environment), these are trusted zones within CPUs. These secure environments offer a harmony between speed and security. Enclaves permit operations on encrypted data without exposing sensitive details. Their access is proliferating across major cloud providers, making them an increasingly sought-after choice for a plethora of applications. However, there’s a catch: users need to place their trust in the Intel-driven technology. This can sometimes interfere with certification journeys and raise eyebrows among potential adopters.
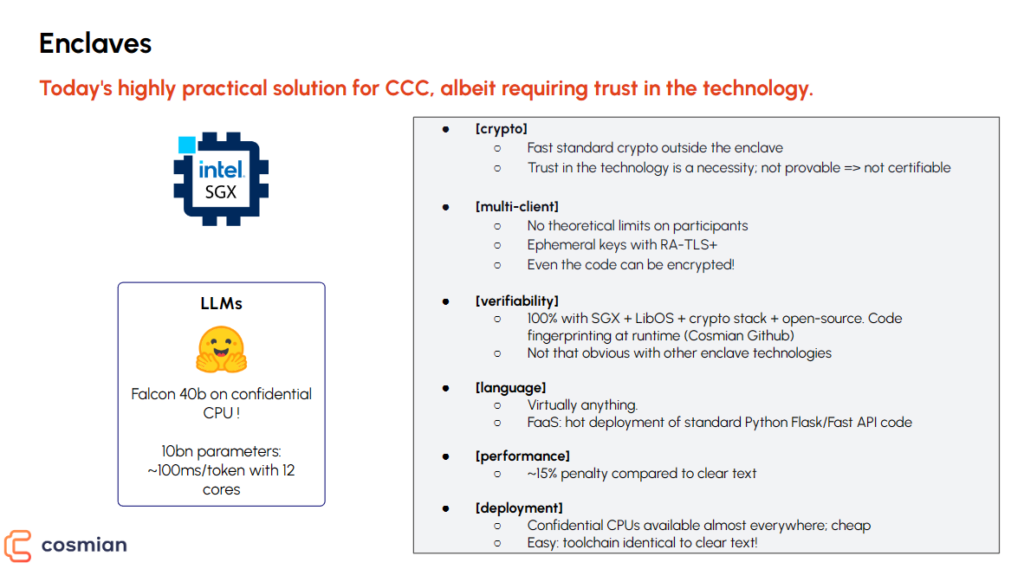
Secure Enclaves: today’s highly practical solution for CCC, albeit requiring trust in the technology.
Future Trajectories:
Confidential computing is spearheading innovations in data security and privacy mechanisms. As sMPC, FHE, and TEE undergo continual refinement, we anticipate seeing a broader application of Collaborative Confidential Computing in various industries.
While TEEs are already a tangible reality, FHE’s potential could be unlocked in the times to come, contingent on research and development strides. In the interim, enterprises can tap into confidential computing capabilities via TEE to protect their sensitive memory spaces and champion secure alliances.