Healthcare
Access sensitive medical data at scale without liability
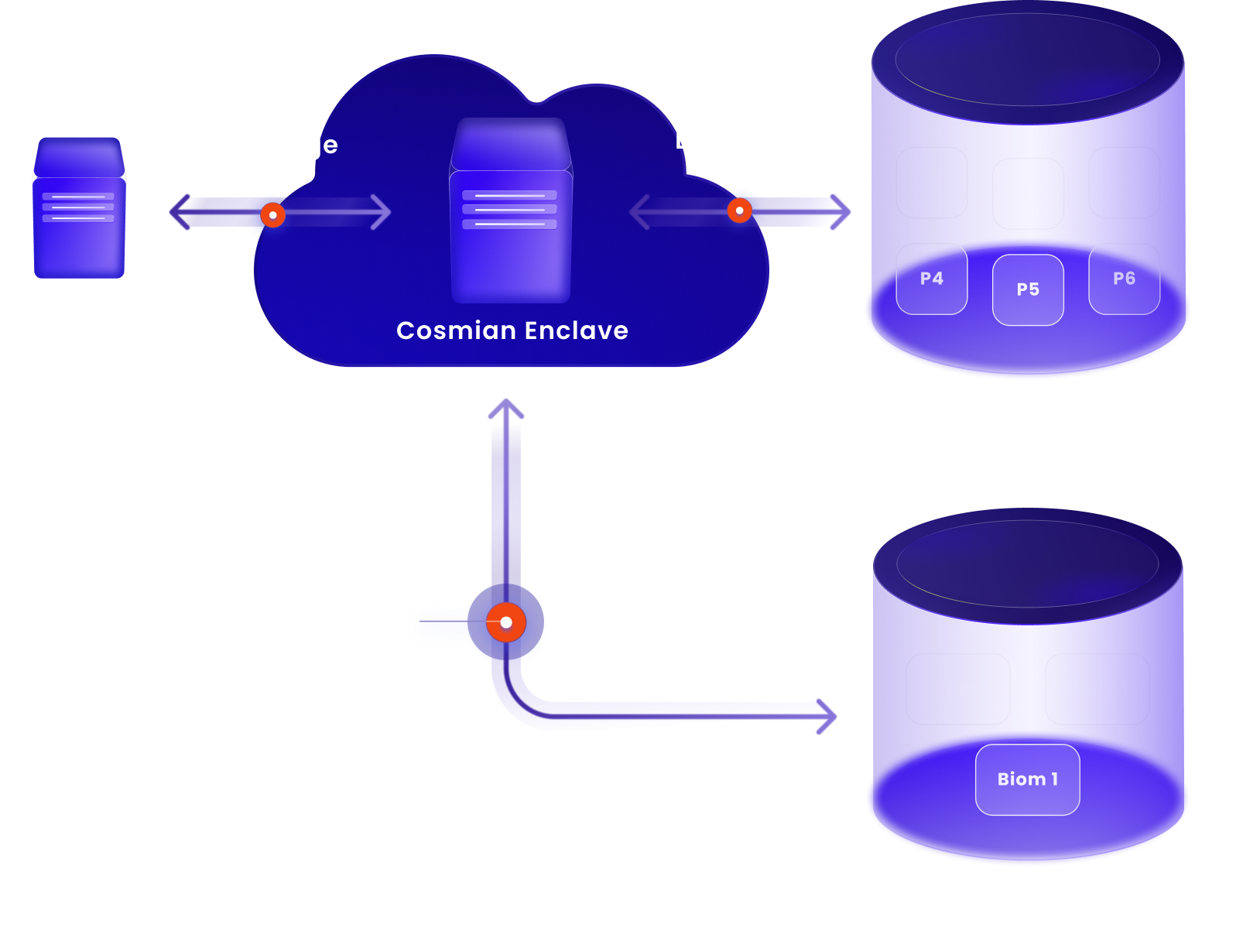
If the first rule in medicine is “Do no harm,” the first rule in health tech is “Protect patient data.” Our technology allows for the extraction of biomarkers in a completely secure environment.
Keep it Confidential with Cosmian.
High performance
on every dimension
The cost of encryption/decryption is now transparent for your IT systems & operations
<5%
overhead
<300µs
Post quantum resistance for Encryption/Decryption speed (0,0003s) for a ciphertext for one partition
+15% max
Ciphertext Expansion compared to cleartext size
More Solutions
Encryption has a lot to offer. Its practical use is put into action every day for businesses and organizations worldwide.
Confidential AI
Keep your data and applications secure when running in cloud environments. Cloud admins won’t learn anything from your data, nor how you use them.
Workplace Applications
Secure your data when used with external, third-party workplace applications such as Google Workspace, and Microsoft Office.
Moving to the cloud
Keep your data and applications secure when running in cloud environments. Cloud admins won’t learn anything from your data, nor how you use them.
Large organisation
Keep your data safe while using third-party applications in your organization.
Manufacturing
Securing information systems for manufacturing operations.
Finance
Financial security starts with secure systems
Data Lakes
Third-Party SaaS
Cloud Native
Offer your customers client-side encryption, and secure your SaaS applications so that cloud providers can’t have access.
Confidential AI
Keep your data and applications secure when running in cloud environments. Cloud admins won’t learn anything from your data, nor how you use them.
Workplace Applications
Keep Secure your data when used with external, third-party workplace applications such as Google Workspace, and Microsoft Office.
Moving to the cloud
Keep your data and applications secure when running in cloud environments. Cloud admins won’t learn anything from your data, nor how you use them.
Large organisations
Keep your data safe while using third-party applications in your organization.
Cloud Native
Offer your customers client-side encryption, and secure your SaaS applications so that cloud providers can’t have access.
Third-Party SaaS
Secure your data in your SaaS applications.
Data lakes
Protect your data lake at scale with custom user-decryption rights and end-to-end encryption between apps.
Finance
Financial security starts with secure systems.
Manufacturing
Securing information systems for manufacturing operations.
High performance
Support any critical application with a 200 to 350 microseconds response time.
Post-quantum Hybridization
AES 256 coupled with CRYSTALS-Kyber & Elliptic curves encryption to ensure the most resilient model, following NIST & National Cyber Security Agency recommendations.
User Access Policies
Asymmetric encryption with multiple decryption keys that contain specific access rights.














