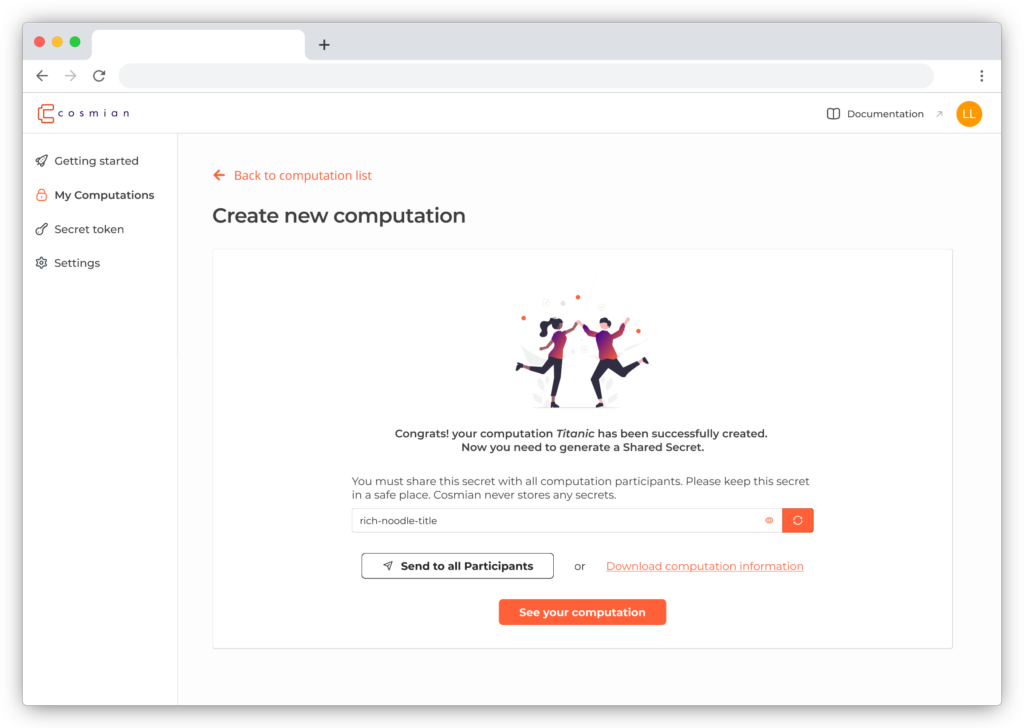
Today, we’re launching a new feature. You can now create a new Secure Computation without installing anything but our Python client.
Why we removed PGP keys
In the previous version of Secure Computation, every participant had to generate a PGP key pair. Then, they could sign any operation with their public key: send encrypted code, encrypted data, or pull the encrypted result.
But generating a PGP key pair requires a third-party tool, like GPG, which creates a lot of friction. You must download, install, and then call it with Python’s subprocess. Pretty inconvenient, right? Since we want to make Secure Computation as easy as possible, we thought hard to find how to remove this step.
All you need is a CryptoContext
Instead of PGP, you can now generate all your keys with Cosmian’s Python Client using our new function CryptoContext(). This function automatically creates:
- an XSalsa20-Poly1305 symmetric key (used to encrypt your code, your data, or to decrypt your result)
- an Ed25519 key pair (used to sign your operation with the enclave)
The code is available publicly on Github, but if you are uber paranoid, you can create the keys yourself.
Pre-Shared Secrets create a zero-trust service
We also used PGP to verify the participants’ identities without relying on Cosmian. Indeed, public servers like keys.openpgp.org let you confirm that you own an email address associated with a public key.
In this new version, we replaced this with Pre-Shared Secrets. A Secure Computation Pre-Shared Secret is a list of three words picked in the BIP39 wordlist and shared between the participants. Since this message does not go through Cosmian services, you can be sure that an attacker cannot impersonate a participant.
Please check our documentation if you want a more detailed overview of our protocol security. And if you need a quickstart example, we also got you covered!
Coming soon
What if you could run a Secure Computation without any client? Soon, you will be able to create a computation, encrypt your code and data, and decrypt your result straight from Cosmian Console.