The quantum wave is changing cybersecurity, bringing excitement and concern to cryptography. Business leaders prepare for a future where company and government data must be even more secure with Post-Quantum encryption. They visualize a digital realm of endless possibilities with the symbolic end of 0s and 1s hegemony.
Quantum computers, utilizing key algorithms rooted in quantum mechanics, promise to solve problems faster than traditional computers. Their capabilities could redefine secure encryption and computation methods. Grasping these security changes is crucial for organizations to support and adapt in our evolving digital age.
Understanding Quantum Computing’s Role in Post-Quantum Encryption
Post-quantum cryptography (PQC) – also called quantum-proof, quantum-safe, or quantum-resistant – is key in modern cryptography.
Quantum computers are underpinned by novel hardware that is set to revolutionize our present computing capabilities. Qubits are at the heart of this transformation, which differ fundamentally from the classical bits in today’s computers. Since existing cryptographic systems rely on intricate mathematical algorithms, quantum computers pose a significant threat to the current encryption paradigms with their unique qubit-based processing. While classical bits can be in one of two states, 0 or 1, qubits, the fundamental unit of quantum information, can exist in multiple states at once. This property known as superposition offers exponentially more computational power.
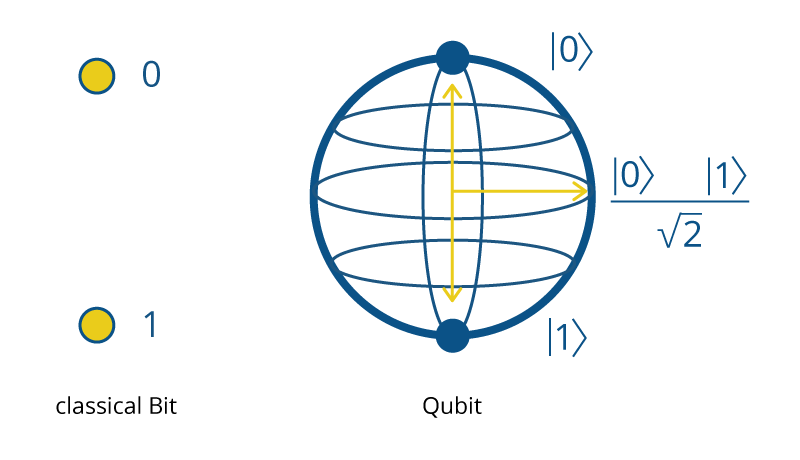
qubits can exist in multiple states known as superposition
National governments in Europe, with France at the forefront, are championing solutions to address these challenges. With companies like Alice & Bob, PASQAL, and Quandela, Europe is demonstrating a strong will to ensure a safe cybersecurity environment for the future. These efforts are a testament to the government’s commitment to crafting robust, national-based solutions in the context of geopolitical tensions.
The Quantum Shift in Cryptography
Cryptography is evolving with quantum technology driving significant changes. These future-oriented machines have the potential to easily decipher algorithms that were once considered secure due to their reliance on challenging mathematical problems. While today’s quantum computers have yet to reach the prowess required to break prevalent encryptions, the cryptographic community isn’t idle. The circulating concept of ‘harvest now, decrypt later’ further underscores the need for action, suggesting that even data encrypted today could be vulnerable in a quantum-rich future.
RSA encryption, for instance, relies on the difficulty of factoring large numbers, a challenge for traditional computers. But with quantum algorithms, RSA encryption becomes vulnerable, and the security keys can be deciphered surprisingly quickly.
This doesn’t mean the end of safe encryption. While public key systems like RSA might be at risk, encryption remains resistant to quantum threats. Highlighting the paradigm shift quantum computers bring, foundational algorithms like Shor’s and Grover’s exemplify the significant advancements over traditional computing methods.
☝ Quantum cryptography
In quantum cryptography, the encryption scheme must be run on a quantum computer. This differs from post-quantum resistance where the encryption scheme runs on a classical computer but is secure if an adversary has a quantum computer.
To keep cryptography relevant in a post-quantum world, we want the encrypted schemes we are using now and running on classical computer code to be resistant in the future, even if the adversary has access to a quantum computer: this is post-quantum security.
- Symmetric cryptography is based on making it hard for someone to guess the key by trying all possible keys. But if someone has a quantum computer, they can guess the key faster using Grover’s algorithm. So, to keep things secure, we need to use longer keys. For example, to get the same security as a 128-bit key, we now need a 256-bit key.
- Asymmetric cryptography is based on tough math problems. It’s easy to decode data if you have the secret key, but hard if you don’t. However, with a quantum computer, some of these math problems become easier to solve. Specifically, Shor’s algorithm can solve problems that RSA and elliptic curve cryptography rely on for their security.
Shaping a Quantum Future in Cryptography
Quantum technology will be revolutionizing the digital domain. It delivers groundbreaking encryption algorithms while simultaneously stretching the established norms of cybersecurity. As the era dominated by quantum computers beckons, fortifying our cryptographic infrastructure and standards is not just essential—it’s imperative, and we urgently need to reinforce our cryptographic standards and infrastructure.
In light of these quantum challenges, the NIST (The US National Institute of Standards and Technology) has been instrumental in developing quantum-resistant cryptographic standards. These standards will represent the future of cryptography, ensuring that both classical and quantum-based threats can be addressed. It’s about learning and adapting to maintain encryption security in this rapidly changing environment.
The tangible progression towards a post-quantum (PQC) future is evident in pioneering endeavors such as Cosmian’s collaboration with NIST “Migration to Post-Quantum Cryptography community of interest, and the ETSI Technical Committee for Cybersecurity to build post-quantum encryption accessible to Fintechs or SaaS applications.
Although the promise of quantum computing is immense, there’s still much to learn. With quantum-resistant algorithms and NIST-backed standards in play, the future of cybersecurity looks promising, safeguarding our data and code against potential quantum threats.

